Hardware locked license keys allow you to limit the use of your license keys to a particular machine/computer and enable copy protection to prevent activated license data from being used on a different machine/computer. In our opinion, a licensing tool with a solid hardware/machine locked licensing feature should have the following :
Secure License Manager, out of the box, supports eight different system identification parameters.
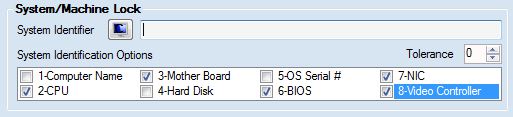
Figure 1. Custom License Data.
To get the system identifier on a given system, you can simply call the SecureLicense.GetSystemId(SystemIdentifierOptions sysIdentifierOptions) method by specifying the SystemIdentifierOptions that you want to use. You can use any combination of the parameters as you see fit in your project. For example, calling secureLicense.GetSystemId(SystemIdentifierOptions.UseProcessorInfo | SystemIdentifierOptions.UseNICInfo) will give you the system identifier using CPU and NIC information.. When generating a license key, if you select CPU and NIC for system identification, the selected parameters values will be used to calculate the system identifier at runtime when attempting to activate a license key. Commonly, it is beneficial to use parameters that do not change often. For example, if an operating system is re-installed, the operating serial number parameter can potentially change. Although it is not common for NIC information to change, it is possible the end users can change their computer's hardware profile by upgrading their NIC.
Optionally, you can provide your own system identifier parameter values. This can be done by overriding the GetSystemIdentifierParts() method. If you override this method, there should at least be one item in they byte array list that is returned. If the byte array list contains more than eight items, all the items after the eighth item will be ignored. The byte array values that are returned must be the same for the same machine/system so that the license validation will return the same result upon subsequent license validation.
You can generate a more restrictive license keys by specifying the system id in the System Identifier input box shown in Figure 1 above. If a license key is generated with a particular system id specified, this license key can only be activated on a machine that has the same system identifier value as the value specified in the system identifier input box. When system identifier validation fails due to hardware profile change (or more specifically, a change in system identifier parameter values), the SecureLicense.IsValid property will return "False". However, in some situations, it is preferred to let the license be considered as valid when only few system identifier parameter values change. This is done by using the Tolerance option. The tolerance option allows you to specify the number of system identifier parameter values that need to change before deeming a license invalid. For example, if you use NIC, BIOS, CPU and Computer Name for system identification and if you define a tolerance value of 2, the license will become invalid only when three of the system identifier parameter values are changed when compared to their initial value that was captured at the time of activating the license key for the first time.
In summary, the following are the key points that you have to consider when implementing hardware/machine locked license keys.
The following are typical steps for using hardware locked license keys